A Client/Server Architecture: the
Client and Management Program.
Network Enforcer is separated into two components - the client
and the management program - and utilizes a client/server architecture.
The client is the workhorse of the Network Enforcer system. It
watches for and enforces filter violations that you have configured.
It keeps track of all behavior filter violations, handles the alerts
and responses, logs the events, and handles remote commands.
The client runs invisibly and cannot be configured or accessed
other than from the management program.
The management program is where you specify what computers you
want to use Network Enforcer on. It allows you to create and configure
filters, perform remote installations, issue remote commands to
the computers running the client, create reports, view logs, and
more. The client computers can only be configured and accessed
from the management program.

Centralized Viewing,
Configuring, Installing, and Monitoring.
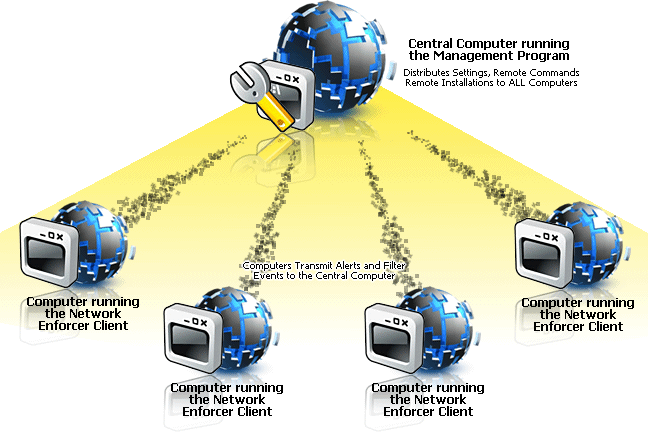
Network Enforcer's architecture allows you to view all computer
filter event logs from one central computer. It also allows you
to distribute settings and filters to all computers at once, or
to specific computers one at a time. Remote commands and realtime
filter alert responses are sent to each computer from the central
computer running the management program. A dedicated server is
NOT needed or necessary for Network Enforcer's management program
to run on.
Customizable, Flexible
Behavior Activity Filters.
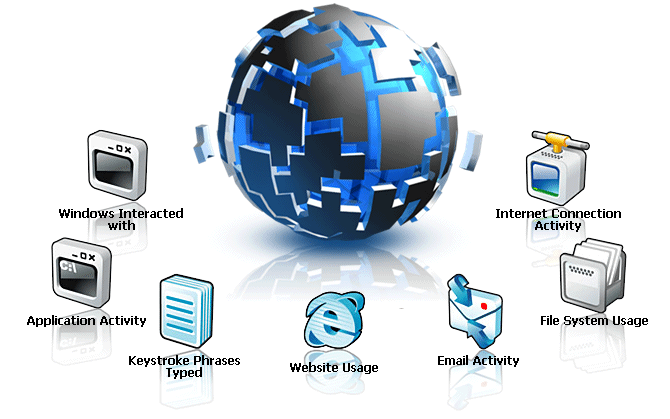
Network Enforcer enforces behavior filters you create, allowing
you to limit and control what happens on your network, or more
specifically, what should NOT happen on your network. Utilizing
three levels of security, each with their own thresholds, filters
can be created to alert you immediately when specific events happen,
or only after they have happened a set number of times. Network
Enforcer allows you to be a little more lenient on the employee
playing solitaire on their lunch break, while being extremely proactive
and reactive on the employee that copies a sensitive file to a
thumb drive. You can configure Network Enforcer to monitor all
the behaviors below for unwanted events.

back to top
|